Managing Authentication Parameters
Authentication parameters are a major stake of account security, especially to guarantee the protection of private data regarding GDPR.
Passwords alone are considered outdated, which is why Actito gives the 'Admin' users of a licence the possibility to set up additional authentication factors.
This is done through the 'Authentication' app of the License configuration portal.
Login page parameters
To choose the authentication mode of the login page, click on 'Edit' in the top right corner.
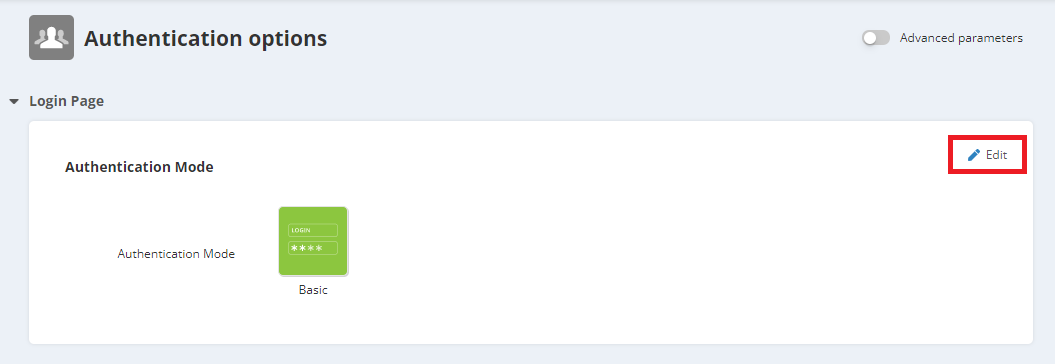
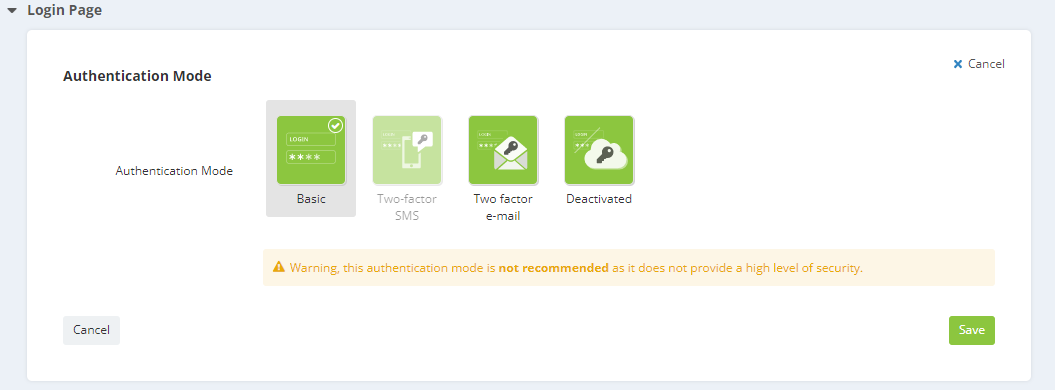
This allows the 'Admin' user to select one of the 4 possible authentication modes.
Basic
The basic authentication mode is the standard process of connecting through a login (user name) and a password.
The password must have a minimum of ten characters and include at least three different character types between:
capital letters
lower case letters
numbers
special characters
Nevertheless, this method is not recommended as it is not considered secure enough compared to others.
Indeed, passwords can be compromised (phishing, repeated use of the same password,...), in which case the basic method does not provide additional guarantees.
Tip
For security reasons, 2-factor authentication is automatically activated at the creation of a new licence.
'Admin' users have the possibility to deactivate it, though we do not recommend doing so.
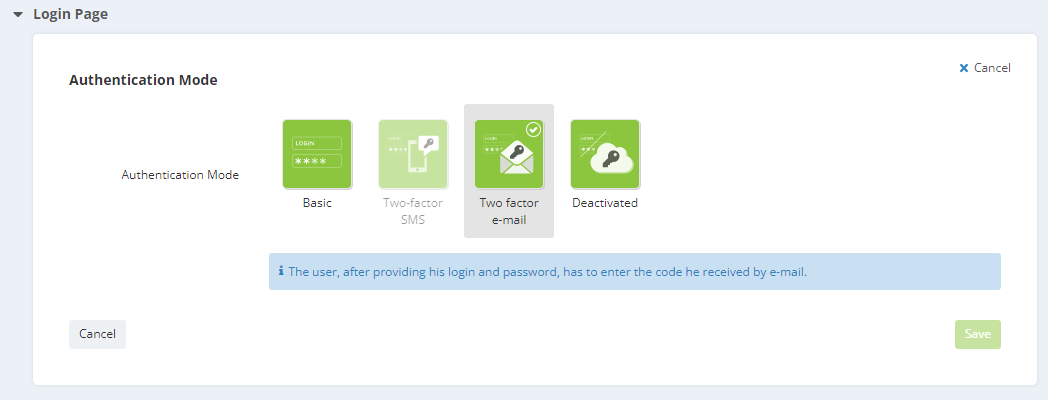
Two-factor authentication (e-mail, SMS or mobile application)
The concept of "two-factor authentication" (or 2FA) consists in multiplying the pieces of evidence required to let a user log in.
To be efficient, the authentication method should combine two factors of different nature :
-
Something the user knows: the principle is identical to standard single factor authentication. This is a password.
-
Something the user has: a one-time code sent to a communication tool belonging to the user. It needs to be provided after the password.
Three options are available for sending the code:
Email 2FA
The code will be sent to the e-mail address associated with the user account. As we strongly advise to only create Actito accounts based on a professional address, anyone who needs to log into the licence will be able to easily retrieve the code on his professional mailbox.
As an e-mail address is required at the creation of any new user, there are no additional pre-requisite to the use of e-mail 2FA. This implies however that the code will be sent to the same resource as the password reminder process.
SMS 2FA
The code will be sent by SMS message to a mobile phone number associated with the user account. Therefore, only someone in possession of the phone will be able to connect to the licence. As mobile phones are usually kept on oneself at all times, this allows to set up strong security without inconveniencing the users.
Prerequisite
To activate SMS two factors authentication, a valid mobile phone number must be linked to each user.
The licence administrator can complete the existing users in the "Manage users" application.
Every new user account must have a valid mobile phone number.
Mobile Application 2FA
The code is found on the mobile authentication application previously installed on the user's phone. All mobile authentication applications are compatible (Google authentication, Sophos, etc.) with Actito 2FA mobile application.
The 2FA by mobile application is more secure than the 2FA by email or sms because it does not require the reception of a code by email or sms. However, the user must configure a mobile authentication application beforehand in order to connect. Moreover, since this authentication mode does not depend on sending a code, no latency in receiving is possible.
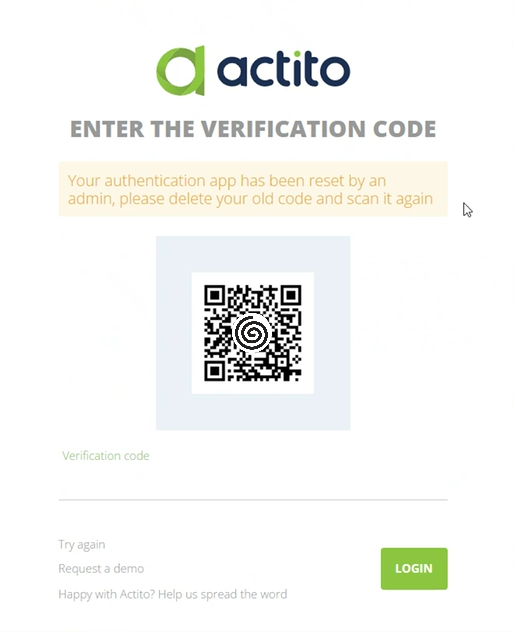
At the first connection, the user will have to scan a QR code via the authentication application with his cell phone. He will then have access to a single-use code. The next time the user logs in, he will no longer have to scan a QR code. He will only have to go on his mobile authentication application to get the password and indicate it on the Actito license connection page.
In your authenticator app, the key will take the name 'login@licence'.
If you have multiple licences with the same name in different environments ( for example, in TEST), we suggest you rename the key accordingly. In most apps, you only need to keep pressing on the key to get the 'edit' button. Indeed, some apps will not allow you to have 2 keys with the same name.
Reset your token
In order to facilitate the management of the 2FA, the Administrator has visibility on the type of 2FA activated for each user.
In the license configuration, the Administrator has access to this information by applying the "authentication mode" filter in the columns or by selecting it in the drop-down menu on the left of the screen.
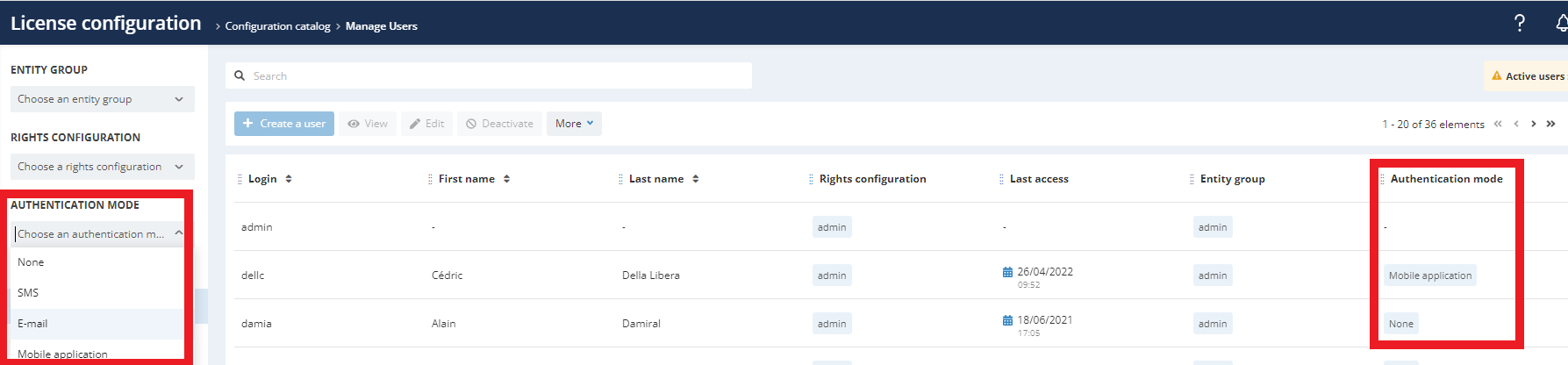
The Administrator has the ability to reset a user's token. That can prove to be useful in the following situations: loss of a cell phone, deletion of the token,...
To do this, he will need to access the License Configuration < More < Token Reset page. This feature exists only for users who use the 2FA mobile application.
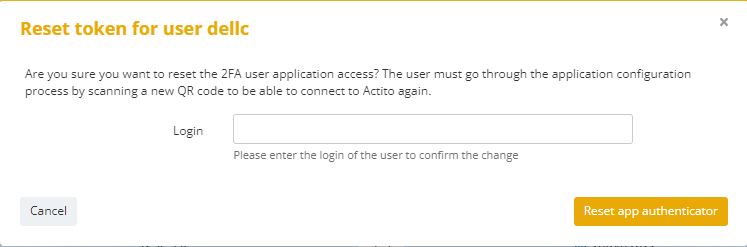
Another page asking for a confirmation of the login of
the user in question will then open.
From the user's perspective, a new QR code will need to be scanned at the time of authentication:
Hierarchy of authentication modes
Depending on the authentication mode selected by the License Administrator, users will be able to choose another authentication mode. However, they will not be able to select a less secure mode than the one predefined.
Here is the classification of the authentication modes in ascending order of security at Actito:
Basic
2FA email
2FA sms
2FA mobile application
Practical Cases
Here are the practical cases:
-
If the Administrator configures the authentication mode as basic for the license, then the user will be able to choose a more secure or the same authentication mode (basic, 2FA email, sms or mobile app).
-
If the Administrator configures the authentication mode to 2FA email for the license, then the user will be able to choose a more secure or identical authentication mode (2FA email, sms or mobile app) but will not be able to switch back to a less secure authentication mode (basic).
-
If the Administrator configures the authentication mode with 2FA sms for the license, then the user will be able to choose a more secure or identical authentication mode (2FA sms or mobile application) but will not be able to switch back to a less secure authentication mode (basic or 2FA email).
-
If the Administrator configures the authentication mode with the 2FA mobile application for the license, then the user will only be able to choose the same authentication mode (because it is the most secure mode) but he will not be able to switch back to a less secure authentication mode (basic, 2FA email or sms).
Logging in
To connect to your licence after activating "2FA", your authentication will be done in 2 steps.
The first one will remain identical to single factor authentication. You need to provide:
The name of licence
Your login (user name)
-
Your password (which is still linked to your e-mail address)

If the login and password combination is correct, you will receive a code by SMS message, by e-mail or in the mobile application and you will be directed towards a second screen (where you'll be reminded of the 2FA mode linked to your account).
Enter the code to access the licence.
In case of incorrect code, you will go back to the first screen and will have to provide your password again.
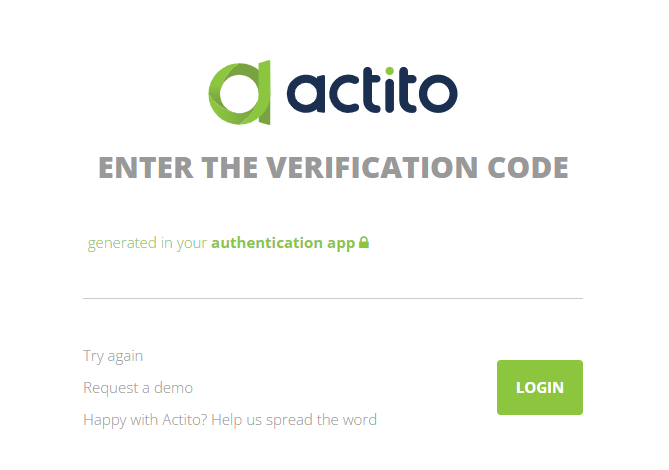
Tip
The code also acts as a warning if someone acquired your password and tries to connect to your account.
If you receive an SMS message or an e-mail while you did not try to log in, please contact security@actito.com and the manager of the licence.
Code validity
Once sent, the code will remain valid for 5 minutes or until the next request (in which case only the new code is valid).
It is possible to request the code to be sent again (once per minute), but it requires you to re-enter your password.
The input of several incorrect codes in a row will temporarily block the user account.
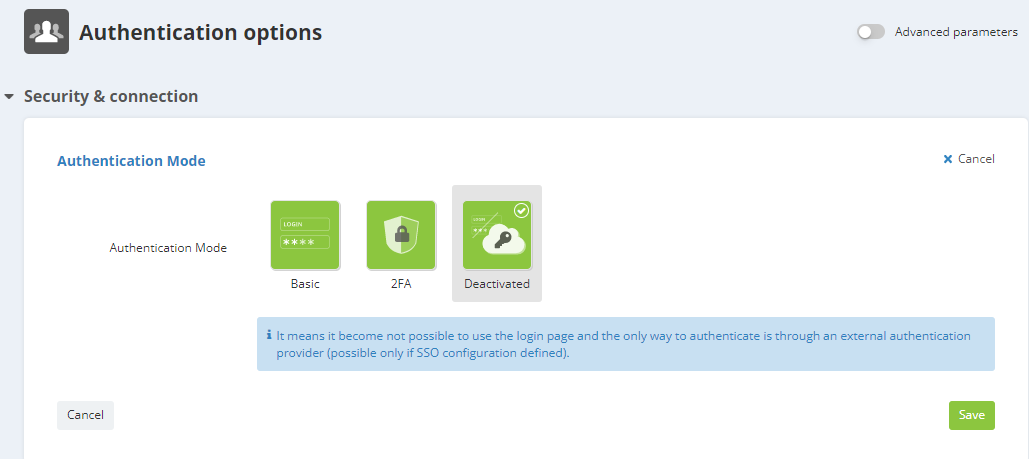
Deactivated
The 'Deactivated' mode means that access through the standard login page is no longer possible.
You can select it only if Single Sign-On (SSO) has been activated and set up in your licence. If it's not the case, the option will be greyed out.
To learn how to activate SSO, please see the next section.
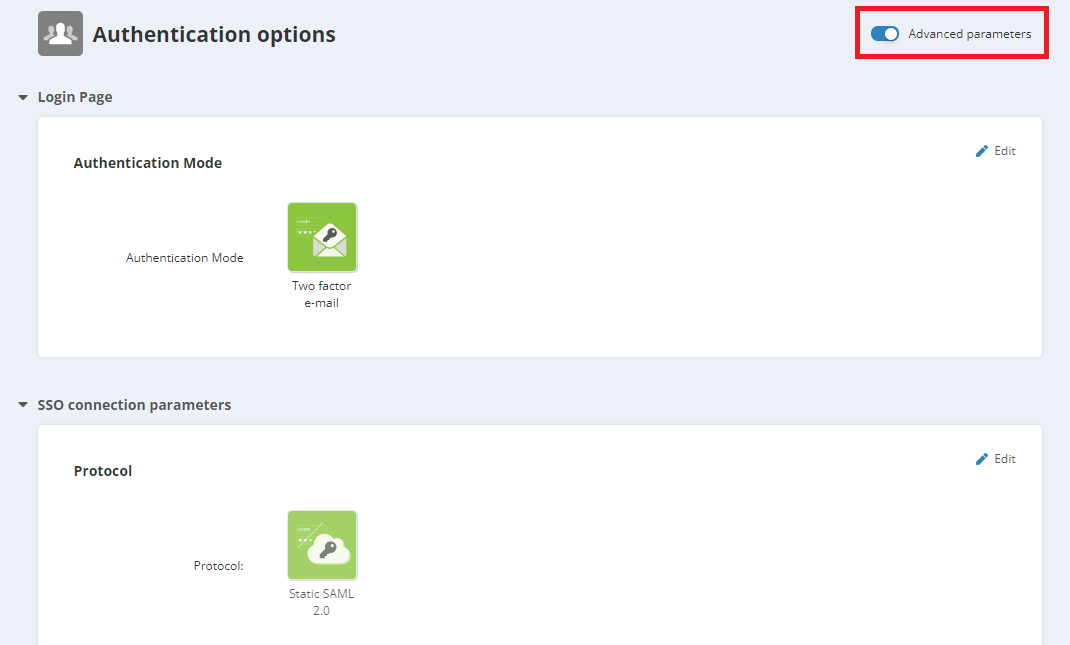
SSO connection parameters (advanced)
Turn on the 'Advanced parameters' to access the 'SSO connection parameters' section.
Good to know
SSO is a billable feature. It is greyed out before its activation.
If you want to use SSO, please contact your account manager.
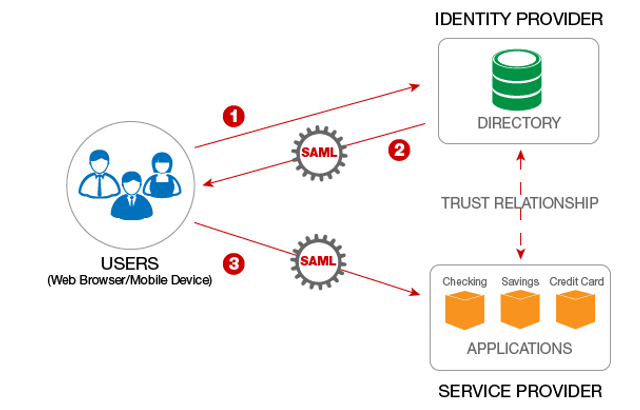
What’s SSO?
Single Sign-On (SSO) is an authentication scheme that allows a user to log in with a single ID and password to any of several related, yet independent, software systems.
Actito only supports SAML 2.0 protocol and Actito is a SAML Service Provider (SP), which means the authentication is made outside of Actito on your side. Then, when the user reaches Actito, Actito will interrogate your SAML Identity Provider (IDP) to have security information on the user and allow him to connect. Both Service and Identity providers must know and trust each other, which means that it requires some technical configuration on both sides.
Pre-requisites
Before starting the SSO configuration, make sure your IDP is compatible with our SSO implementation. You will need to confirm the below elements with your technical operator:
-
Your Identity provider (IDP) supports SAML 2.0
-
The mapping between IDP users and Actito users can be done with the users’ e-mail address
-
The IDP can provide the e-mail address of users in its assertions.
Configuring SSO access
Click on 'Edit' in the top right corner to start the configuration of SSO parameters.
Good to know
Only one section can be edited at a time. You should close the 'Login page' edition mode before editing SSO parameters.
Protocol
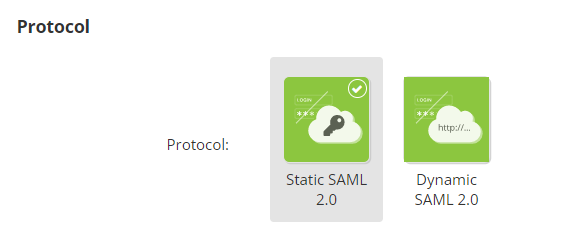
The only protocol supported by the Actito SSO is SAML 2.0. The difference here is between providing the metadata of the IDP statically or dynamically.
To complete the configuration, the metadata of your IDP must be available to be coupled with the Actito metadata.
There are several possibilities for this:
-
Static SAML 2.0: the metadata of the IDP will have to be entered manually, or by uploading an XML file. If the metadata change on your side, it will have to be updated manually in Actito.
-
Dynamic SAML 2.0: the metadata of the IDP must be available on a public URL. If the metadata change on your side, any update will be reflected through the URL.
The information needed for the next section depends on the protocol.
SAML metadata (Static)
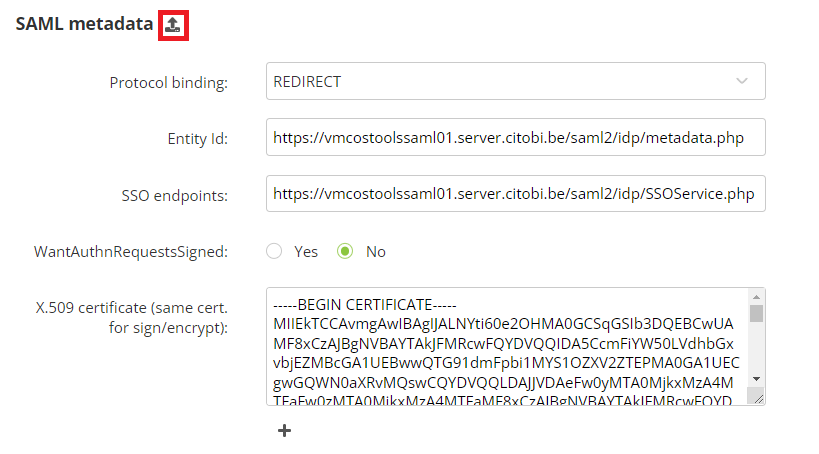
The easiest way to provide the IDP metadata is by uploading an XML file.
This is done by clicking on the icon next to the header of the section. This will allow you to load a file from your computer to automatically fill the required parameters.
Otherwise, it is also possible to enter the parameters manually:
-
Protocol binding: this is the method used for communications between the SP and IDP, including the authentication request. It can be either REDIRECT (GET) or POST.
-
Entity Id: the entity Id is the globally unique and immutable name for a SAML entity. While it does not need to be a web location, it should usually be an absolute URL starting with 'https://'.
-
SSO endpoints: t he URL of the SAML 2.0 implementation that receives authentication requests for processing. It must be a valid URL starting with 'http://' or 'https://' (https is advised).
-
WantAuthnRequestsSigned: this specifies whether the IDP (your application) requires the authentication requests received from the SP (Actito) to be signed (Yes) or not (No).
-
X.509 certificate (same cert. for sign/encrypt): the certificates used by the IDP to sign SAML assertions, so that the SP can validate its authenticity. Several certificates can be added. The same certificate will be used for signing and encryption.
SAML metadata (Dynamic)
Most of the information is provided through the public metadata URL, which means any update to the SSO configuration is applied immediately when the metadata is updated on the URL.
You need to provide the following parameters:
-
Protocol binding: this is the method used for communications between the SP and IDP, including the authentication request. It can be either REDIRECT (GET) or POST
-
Entity Id: the entity Id is the globally unique and immutable name for a SAML entity. While it does not need to be a web location, it should usually be an absolute URL starting with 'https://'.
-
Metadata url: the public URL containing the metadata of your IDP.
Mapping with actito users
The last section is common to both static and dynamic protocols.
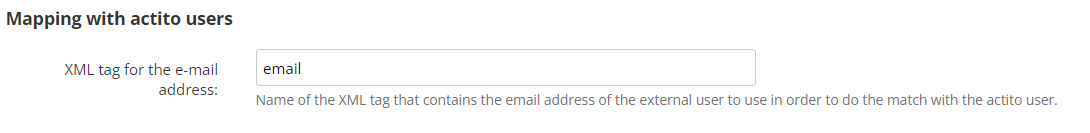
It is used to provide the XML tag that corresponds to a user's e-mail address in the IDP configuration. It will be used to match the external user logged through SSO with the Actito user.
The matching key must be the e-mail address.
Good to know
A user must be created in the Actito licence by the 'Admin' user. Otherwise, the e-mail address will not match and SSO will not work.
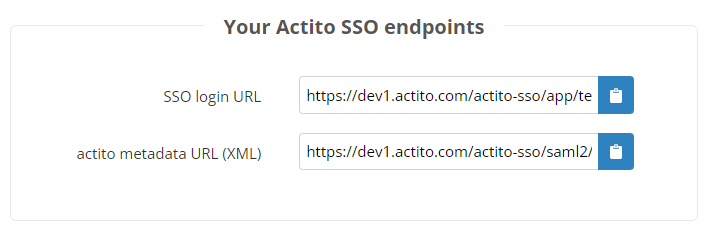
Your Actito SSO endpoints
Once you save the SSO configuration, you will exit 'Edit' mode, see the information you provided as well the information that you need from Actito to connect through SSO.
These are:
-
SSO login URL: the URL that you can use to connect to Actito after logging in your IDP platform.
It will always have the following structure: https://<actitoHost>/actito-sso/app/<licenseName>
-
actito metadata URL (XML): the metadata of Actito as SP (in XML format), to provide in your IDP.
The URL will always have the following structure : https://<actitoHost>/actito-sso/saml2/service-provider-metadata/<licenceName>
The variables in the URLs are:
-
actitoHost: depends on the environment of the licence (www.actito.be, www1.actito.com or www3.actito.com, same as the domain of the user platform)
-
licenceName: the name of the licence to configure.
Tip
Only one IDP can be used per licence.
Once SSO has been configured, you can choose to entirely disable the login page for your licence, to only allow login through SSO (see 'Deactivated' option above).
